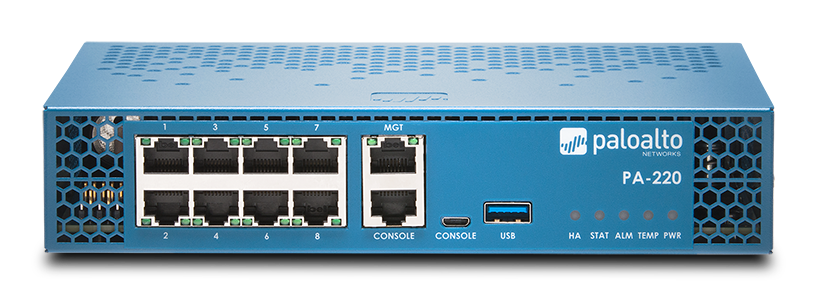
Active passive and active active high availability ha passive cooling no fans to reduce noise and power consumption eight ethernet ports and dual power adapters for power redundancy.
Palo alto pa 220 power supply.
To provide power redundancy for the firewall prepare two additional dc power cables to connect the second set of dc power inputs.
To avoid injury to yourself or damage to your palo alto networks hardware or the data that resides on the hardware read the product safety warnings.
Ac power adapter for pa 220 pan pa 220 pwr ac.
Contact your zones account manager or call 800 408 9663.
The palo alto networks pa 3200 series next generation firewalls are designed for data center and internet gateway deployments.
Other users also viewed.
As a member you ll get exclusive invites to events unit 42 threat alerts and cybersecurity tips delivered to your inbox.
You will need one ground cable and two dc cables one for the positive connection and one for the negative connection.
The palo alto networks pa 220 next generation firewall is designed for small organizations or branch offices and includes the following main features.
Pa 220 firewall pa 220r firewall pa 3000 series.
To avoid injury to yourself or damage to your palo alto networks hardware or the data that resides on the hardware read the product safety warnings.
These models provide flexibility in performance and redundancy to help you meet your deployment requirements.
This series is comprised of the pa 3260 pa 3260 and pa 3260 firewalls.
See the document troubleshooting palo alto networks hardware issues.
The following procedure describes how to connect power to a pa 220 firewall.
Unplug the failed power adapter from the ac power source and then turn the power cable connector nut on the back of the firewall pwr1 or pwr2 counterclockwise to release the cable.
Show system environmentals power supplies slot description alarm inserted s1 power supply 1 left false.
The controlling element of the palo alto networks pa 220 is pan os security operating system which natively classifies all traffic inclusive of applications threats and content and then ties that traffic to the user regardless of location or device type.